The client has a site to site VPN connecting two offices. When owner uses VPN client establishing connection to one of office (OfficeA), he can’t RDP to the servers in second office (OfficeB). I assume we need to add NAT and access list, but don’t know how to do it. I know little about ASDM. Attached is the configuration file. Any help will be appreciated. This is configuration
name 172.31.31.0 inside-voice
name 10.100.1.0 anyconnect-network description anyconnect dhcp pool network
name 192.168.1.2 CallManager description Call Manager Express
ip local pool IPSEC_DHCP 192.168.200.100-192.168.200.200 mask 255.255.255.0
ip local pool anyconnect_pool 10.100.1.1-10.100.1.25 mask 255.255.255.0
access-list inside_access_in extended permit ip any4 any4
access-list inside_access_in extended permit icmp any4 any4
access-list inside_nat0_outbound extended permit ip 192.168.0.0 255.255.0.0 192.168.0.0 255.255.0.0
access-list inside_nat0_outbound extended permit ip 172.31.0.0 255.255.0.0 192.168.0.0 255.255.0.0
access-list inside_nat0_outbound extended permit ip 10.254.254.0 255.255.255.0 192.168.0.0 255.255.0.0
access-list inside_nat0_outbound extended permit ip 192.168.0.0 255.255.0.0 172.34.0.0 255.255.0.0
access-list inside_nat0_outbound extended permit ip 172.31.0.0 255.255.0.0 172.34.0.0 255.255.0.0
access-list inside_nat0_outbound extended permit ip 10.254.254.0 255.255.255.0 172.34.0.0 255.255.0.0
access-list inside_nat0_outbound extended permit ip 192.168.1.0 255.255.255.0 object anyconnect-network
access-list remote_VPN extended permit ip 192.168.0.0 255.255.0.0 any4
access-list remote_VPN extended permit ip 172.31.0.0 255.255.0.0 any4
access-list remote_VPN extended permit ip 10.254.254.0 255.255.255.0 any4
access-list split-tunnel standard permit 192.168.1.0 255.255.255.0
access-list outside_access_in extended permit icmp any4 any4
access-list outside_access_in extended permit ip any4 host x.x.2.138
access-list outside_access_in extended permit icmp any4 host x.x.2.138
access-list outside_access_in extended permit ip host x.x.193.56 any4
access-list outside_access_in extended permit object-group DM_INLINE_PROTOCOL_1 object-group momentum_networks object CallManager
access-list outside_cryptomap_1 extended permit ip 192.168.1.0 255.255.255.0 192.168.0.0 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside
asdm image disk0:/asdm-761.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,any) source static obj-172.31.0.0 obj-172.31.0.0 destination static obj-192.168.0.0 obj-192.168.0.0 no-proxy-arp route-lookup
nat (inside,any) source static obj-10.254.254.0 obj-10.254.254.0 destination static obj-192.168.0.0 obj-192.168.0.0 no-proxy-arp route-lookup
nat (inside,any) source static obj-172.31.0.0 obj-172.31.0.0 destination static obj-172.34.0.0 obj-172.34.0.0 no-proxy-arp route-lookup
nat (inside,any) source static obj-10.254.254.0 obj-10.254.254.0 destination static obj-172.34.0.0 obj-172.34.0.0 no-proxy-arp route-lookup
nat (inside,any) source static obj-192.168.1.0 obj-192.168.1.0 destination static anyconnect-network anyconnect-network no-proxy-arp route-lookup
nat (inside,4G-LTE) source static CallManager interface service CME1 CME1
nat (inside,outside) source static CallManager interface service CME1 CME1
nat (inside,outside) source static NETWORK_OBJ_192.168.1.0_24 NETWORK_OBJ_192.168.1.0_24 destination static NETWORK_OBJ_192.168.0.0_24 NETWORK_OBJ_192.168.0.0_24 no-proxy-arp route-lookup
!
object network obj_any
nat (inside,outside) dynamic interface
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 x.x.2.142 1 track 1
route 4G-LTE 0.0.0.0 0.0.0.0 192.168.101.1 254
route inside 10.254.254.0 255.255.255.0 CallManager 1
route inside inside-voice 255.255.255.0 CallManager 1
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map outside_dyn_map 20 set ikev1 transform-set ESP-3DES-SHA ESP-AES-256-SHA
crypto dynamic-map outside_dyn_map 20 set security-association lifetime seconds 28800
crypto dynamic-map outside_dyn_map 20 set security-association lifetime kilobytes 4608000
crypto map outside_map 1 match address outside_cryptomap_1
crypto map outside_map 1 set peer x.x.76.27
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 1 set ikev2 ipsec-proposal DES 3DES AES AES192 AES256
crypto map outside_map 65535 ipsec-isakmp dynamic outside_dyn_map
crypto map outside_map interface outside
crypto ca trustpoint localtrust
enrollment self
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint2
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint3
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint4
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint5
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint6
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint7
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint0
enrollment terminal
fqdn bobvpn.chicagotech.com
subject-name CN=bobvpn.ms-mvps.com,O=”chicagotech”,C=US,St=IL
keypair bobanyconnect
crl configure
crypto ca trustpoint ASDM_TrustPoint8
crl configure
crypto ca trustpoint ASDM_TrustPoint9
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint10
crl configure
crypto ca trustpoint ASDM_TrustPoint11
crl configure
crypto ca trustpoint ASDM_TrustPoint12
enrollment terminal
subject-name CN=chicagotech
keypair bobvpn.ms-mvps.com
crl configure
crypto ca trustpool policy
crypto isakmp identity address
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 20
authentication pre-share
encryption aes
hash sha
group 1
lifetime 86400
crypto ikev1 policy 25
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 30
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
crypto ikev1 policy 65010
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 2147483647
Author: Admin
How to decrypt Rapid Ransomware files
Workaround 1: Use file recovery software
It’s important to know that the .rapid ransomware creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Data Recovery Pro for this purpose. The newest version of the ransomware under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.
Previous Versions
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.
SQL server connection issue with multiple errors
Situation: The client has SQL Server 2005 on Windows 2008 R2. The SQL seems to have a connection issue with these error:
System.Data.SqlClient.SqlException: SQL Network Interface: error Location Server/Instance Specified [xFFFFFFFF]
Login timeout expired.
An error has occurred while establishing a connection to the server.
How to stop Windows backup
Situation: the client runs Windows Backup on their Windows 2012 R2 server. It stays on 75% completed and their SQL server has a problem.
Resolution: Stop the windows backup by run this command: wbadmin stop job
This is the result:
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\Administrator>wbadmin stop job
wbadmin 1.0 – Backup command-line tool
(C) Copyright 2004 Microsoft Corp.
Are you sure you want to stop the current operation?
[Y] Yes [N] No y
The backup operation ended before completing.
C:\Users\Administrator>
How to restore OneDrive data
To restore deleted items from Microsoft OneDrive website:
1. Login Office 365
2. On the left pane, tap or click Recycle bin.
3. To restore all items, click Settings icon and then Restore.
Google Custom Search requires JavaScript
Situation: When user use Google custom search, he gets this message:
Google Custom Search requires JavaScript
JavaScript is either disabled or not supported by your browser. To use Custom Search, enable JavaScript by changing your browser options and reloading this page
Resolution: To allow all websites within the Internet zone to run scripts within Internet Explorer:
1.On the web browser menu, click Tools or the “Tools” icon (which looks like a gear), and select Internet Options.
2.When the “Internet Options” window opens, select the Security tab.
3.On the “Security” tab, make sure the Internet zone is selected, and then click on the “Custom level…” button.
4.In the Security Settings – Internet Zone dialog box, click Enable for Active Scripting in the Scripting section.
In the Security Settings – Internet Zone dialog box, click Enable for Active Scripting in the Scripting section.
5.When the “Warning!” window opens and asks, “Are you sure you want to change the settings for this zone?” select Yes.
6.Click OK at the bottom of the Internet Options window to close the dialog.
7.Click the Refresh button to refresh the page and run scripts.
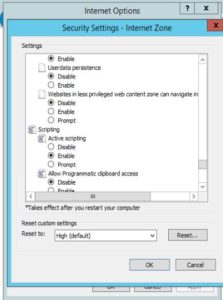
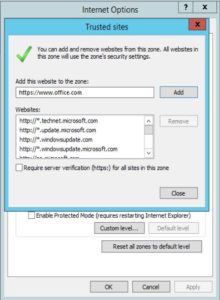
Also you may want to allow scripting on a specific website, while leaving scripting disabled in the Internet zone, add the specific Web site to the Trusted sites zone:
Can’t access phpBB forums with Deprecated error
After I installed WordPress, people can’t access all my phpBB forums with this message:
Deprecated: Methods with the same name as their class will not be constructors in a future version of PHP; acm has a deprecated constructor in /home4/chicagot/public_html/netforums/includes/acm/acm_file.php on line 23
Deprecated: Methods with the same name as their class will not be constructors in a future version of PHP; user has a deprecated constructor in /home4/chicagot/public_html/netforums/includes/session.php on line 1423
Deprecated: Methods with the same name as their class will not be constructors in a future version of PHP; bitfield has a deprecated constructor in /home4/chicagot/public_html/netforums/includes/functions_content.php on line 1233
Deprecated: Methods with the same name as their class will not be constructors in a future version of PHP; dbal has a deprecated constructor in /home4/chicagot/public_html/netforums/includes/db/dbal.php on line 23
Fatal error: Uncaught Error: Call to undefined function mysql_connect() in /home4/chicagot/public_html/netforums/includes/db/mysql.php:47 Stack trace: #0 /home4/chicagot/public_html/netforums/common.php(213): dbal_mysql->sql_connect(‘localhost’, ‘chicagot_pbb01’, ‘ropDiBkgko’, ‘chicagot_pbb01’, ”, false, false) #1 /home4/chicagot/public_html/netforums/index.php(20): include(‘/home4/chicagot…’) #2 {main} thrown in /home4/chicagot/public_html/netforums/includes/db/mysql.php on line 47
I have restored it using hosting backup, but that doesn’t fix the problem. Help please.
How to setup public in WordPress Privacy
I just installed WordPress 4.9.7 and want that public can view it. When I open it, http://www.chicagotech.net/WordPress (it is no http://www.chicagotech.net/WordPress/WP-Admin), it popup for credentials to login. Any blog I published need to login to be viewed.
I assume I need to setup public in Privacy. However, if I go to Settings>Privacy, I don’t see any options for public. Why?
Can’t access Cisco SG300 switch
Situation: The client was working on Cisco SG300 switch and it works. After they moved the switch, they can’t access the switch any more. Can’t ping or GUI into. However, they can access it using console port and see the port is up.
Troubleshooting: 1. Is the port up yes – “show int sttaus” shows
gi48 full 100 enabled up.
2. Which VLAN used gi48? show vlan shows VLAN 10
vlan 1 untagged port gi1-47
vlan 10 untagged port 48
3. The client only uses VLAN 1 (192.168.16.0/24) now. “show ip int” shows VAL 1 operation is down.
192.168.15.2/24 vlan 10 up/up
192.168.16.2/24 vlan 1 up/down
Resolution: Change port from VLAN 10 to VLAN 1 fixing the problem:
config
int gi48
switchport access vlan 1
What and why use DHCP Relay Agent
A DHCP relay agent is a small program that relays DHCP/BOOTP messages between clients and servers on different subnets. To support and use DHCP service across multiple subnets, the router(s) that connect each subnet must support DHCP/BOOTP relay agent capabilities.
By default DHCP works via broadcasting on the local subnet and therefore is limited to being able to provide IP addresses for devices on its subnet only. In modern day networks this is a serious limitation as it would mean that for every subnet you would need a DHCP server – imagine the management overhead!
So how can we configure a DHCP server in one subnet to respond and provide IP addresses to clients in multiple other subnets? The answer is to use a DHCP Relay Agent.