With Palo Firewall open, click Monitor, you can do these:
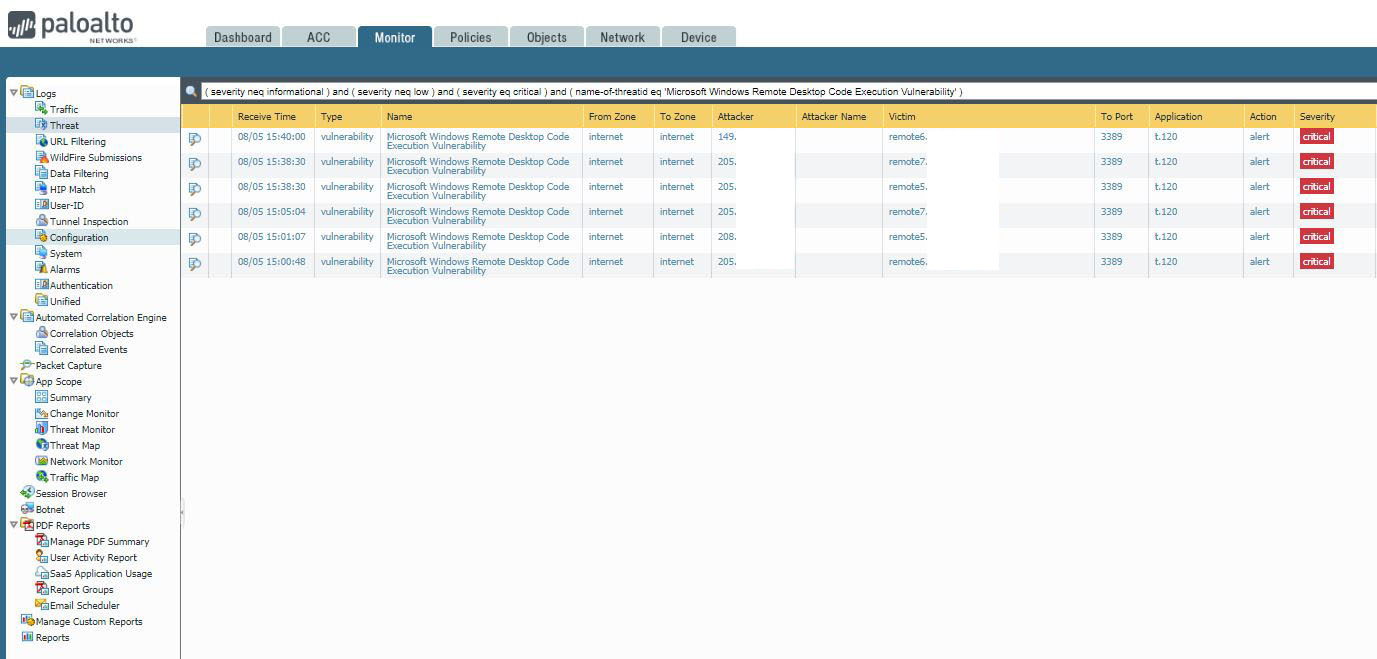
Logs of Traffic, Threat, URL filtering, configuration, system.
Summary of App Scope, Top 10 Apps, Top 10 Threats, Network Monitor of Applications,
PDF Reports, and reports.
Author: Admin
What can Threat Activity do in Palo ACC
1. We can view Threat Activity and Compromised Hosts.
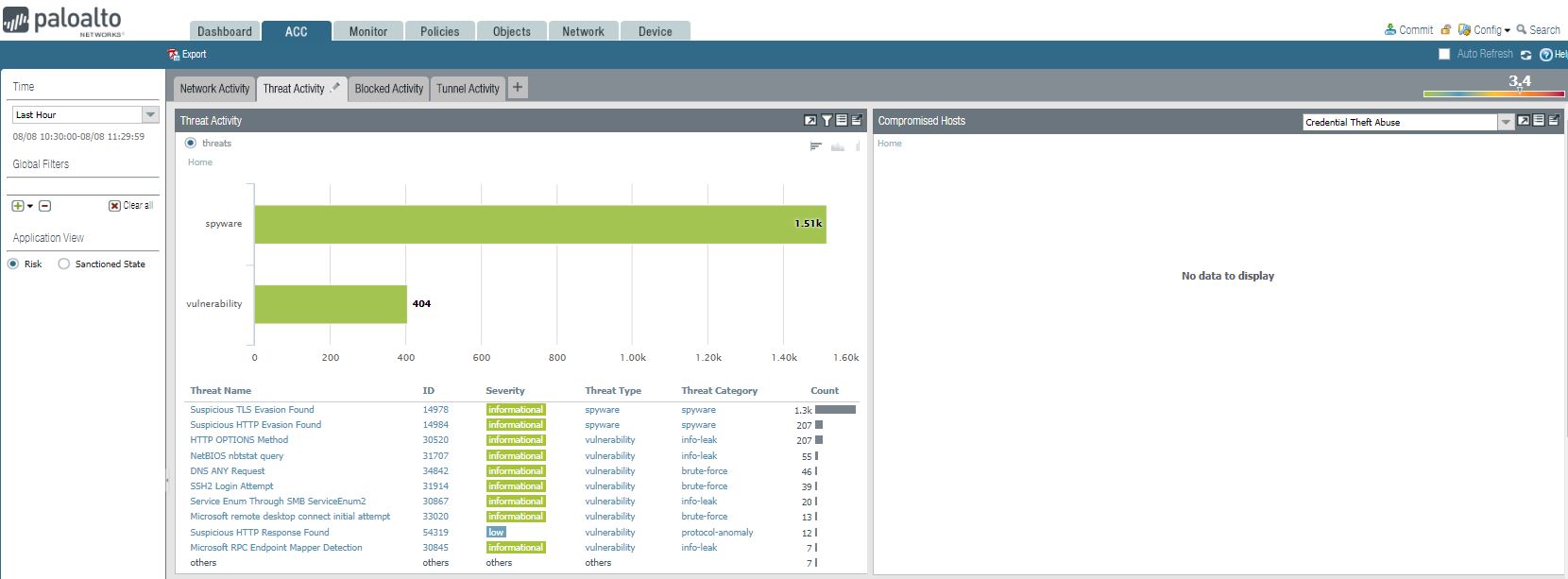
2. We can view WildFire Activity by File Type and WildFire Activity By Application.
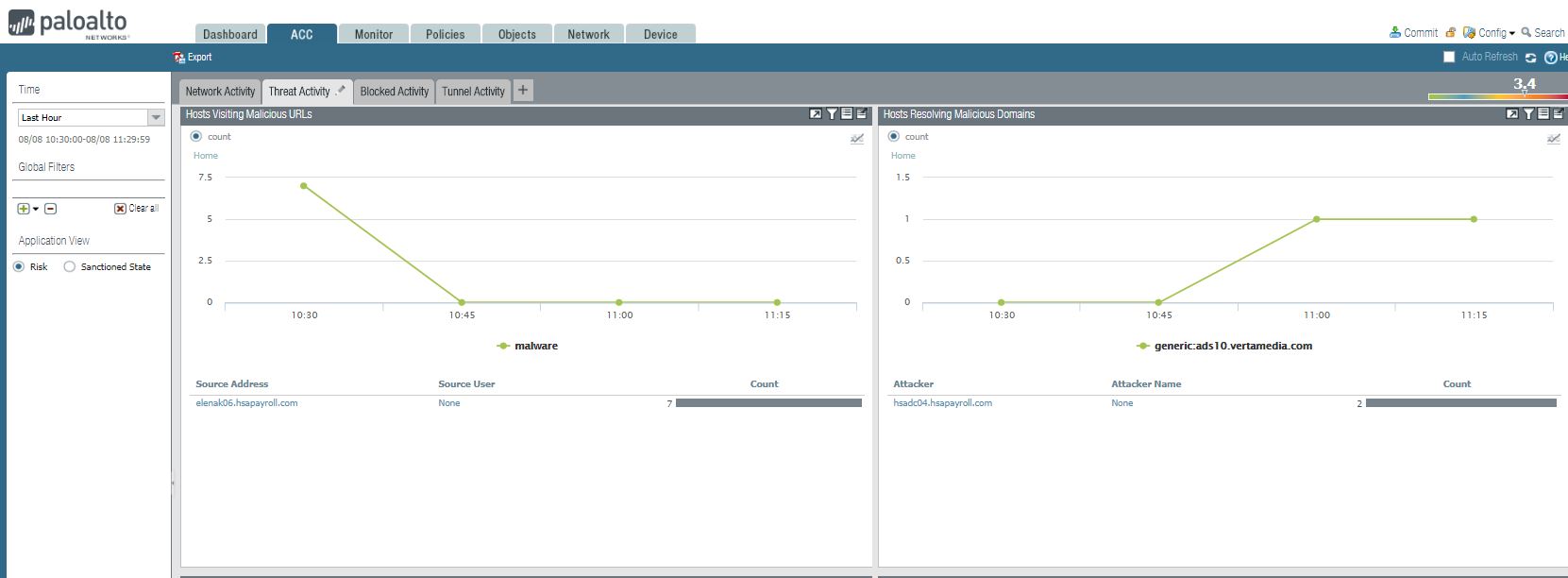
3. Hosts Visiting Malicious URLs and Host Resolving Malicious Domains.
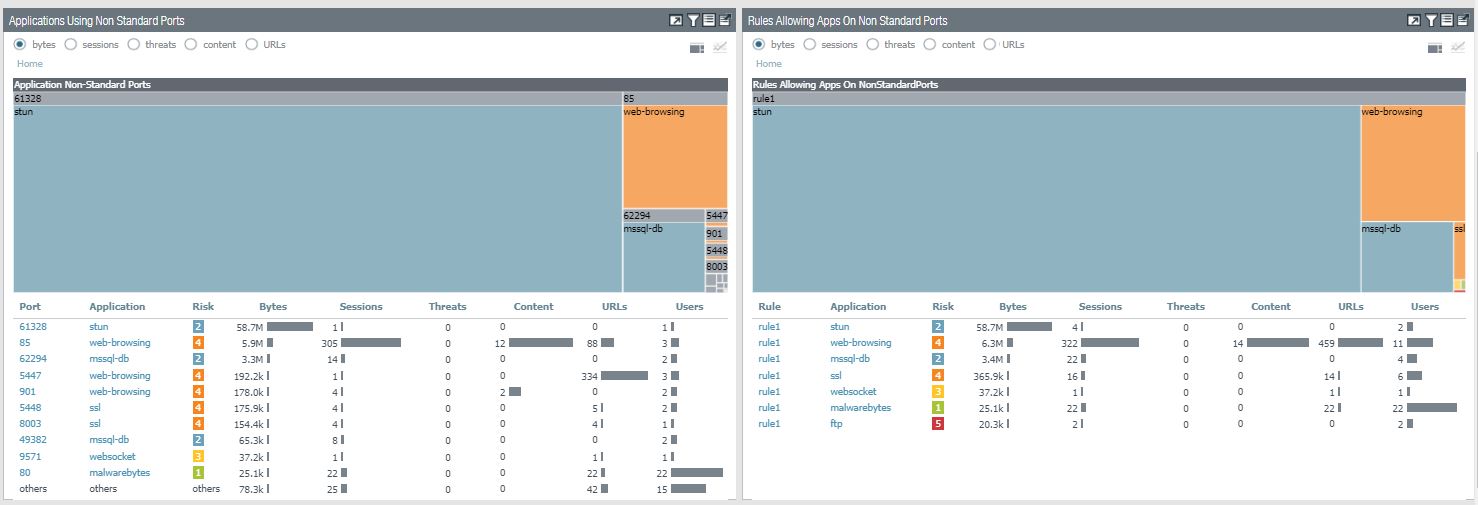
4. Applications Using non Standard Ports and rules Allowing Apps On Non Standard Ports
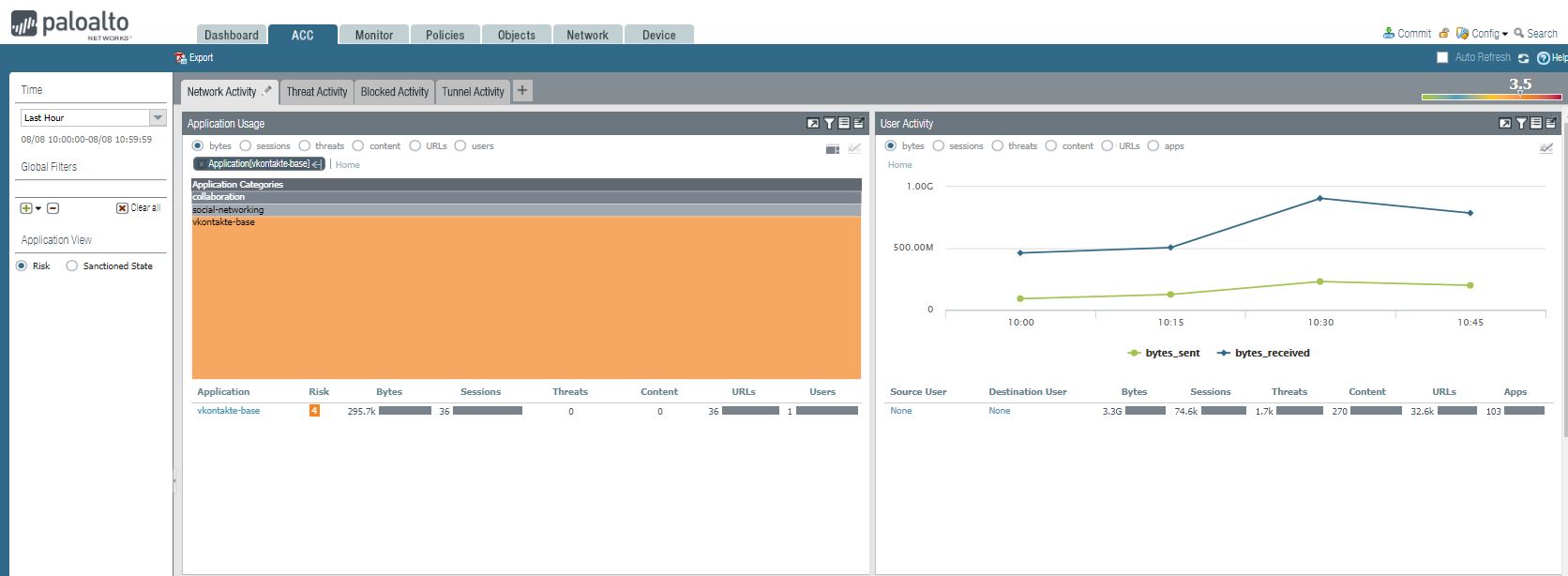
Network Activity under Palo ACC
From Palo ACC screen, you can view these information:
1. Application Usage such as Application, Risk Bytes, Session, Threats URLs and users. user Activity such as Source User, Destination User, Bytes, Sessions, Threat, URLs, and Apps.
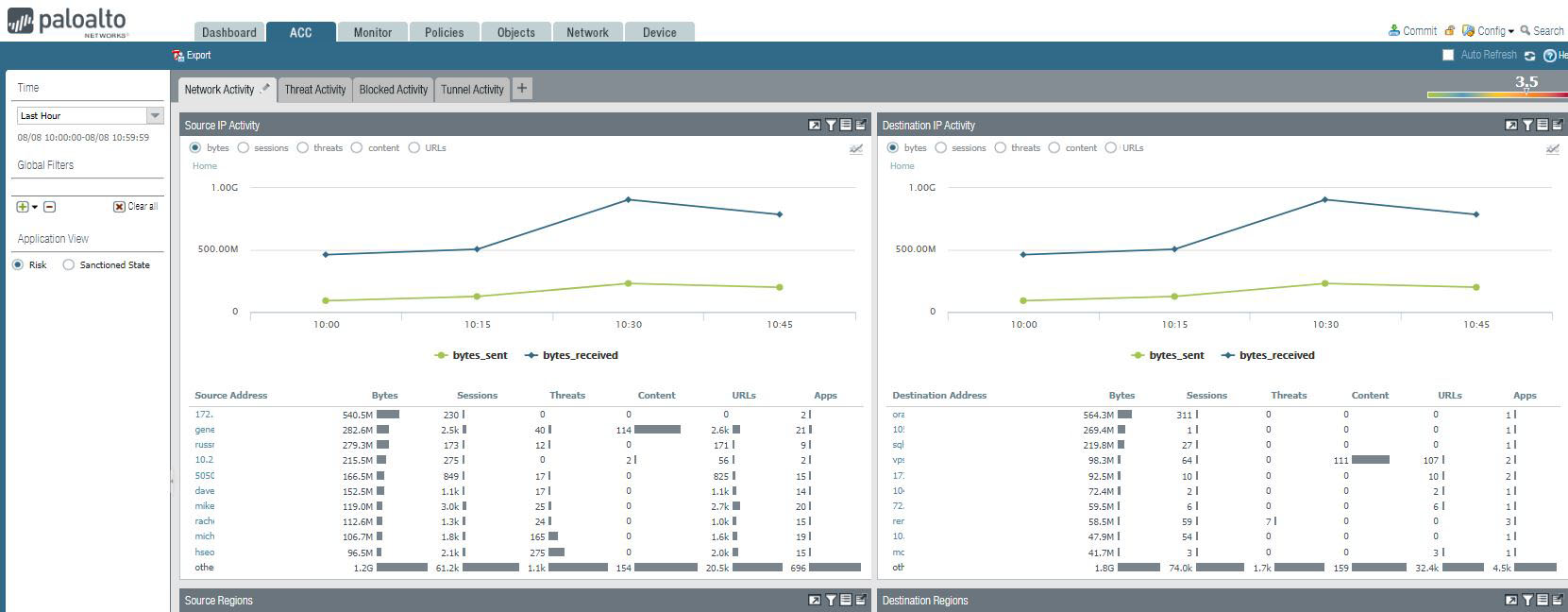
2. Source IP Activity shows Source address or DNS information.
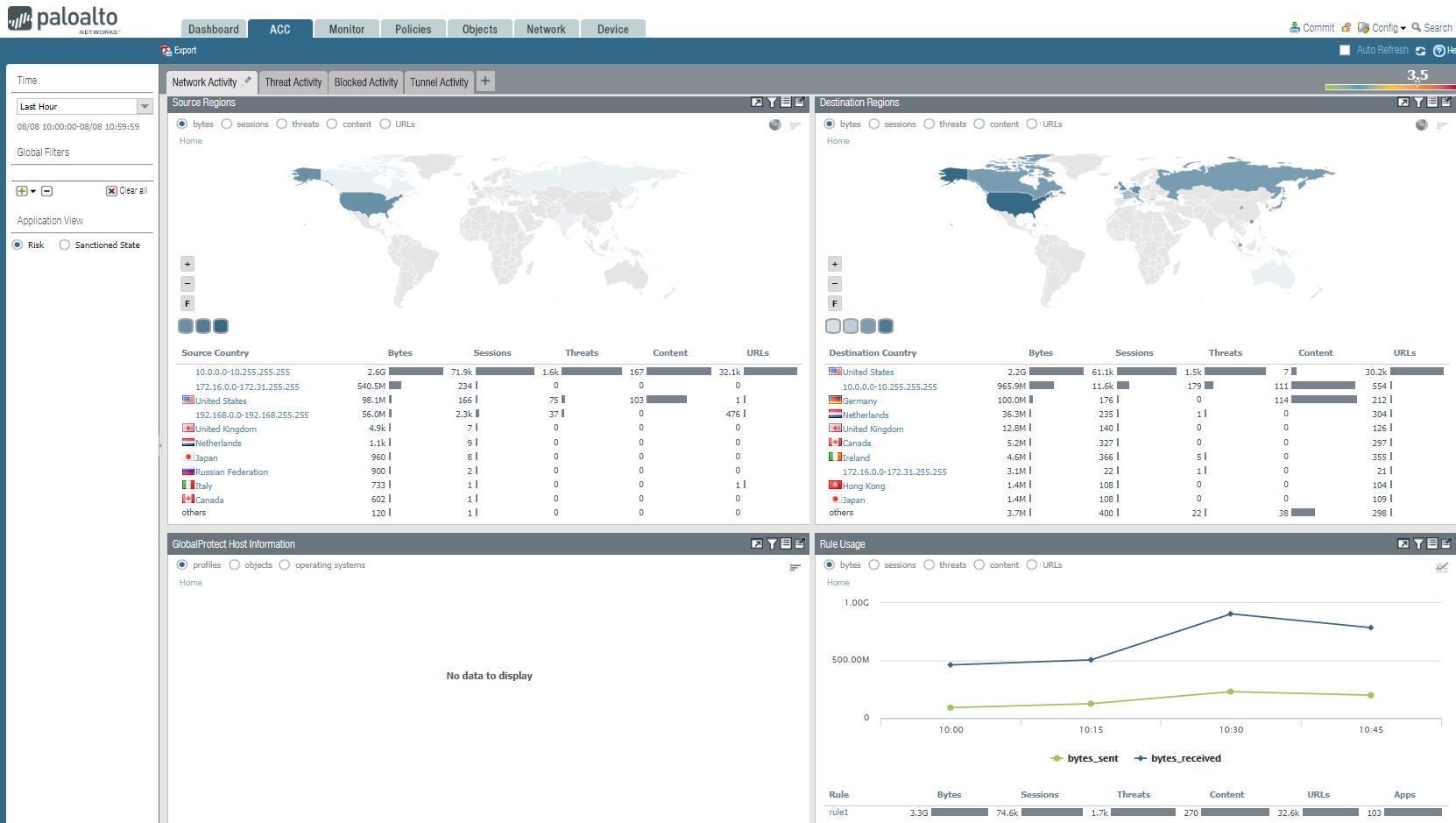
3. Network Activity also shows these information: Source Regions, Destination Regions, GlobalProtection Host Information, and Rule Usage.
Overview of Paloalto Dashboard
After login Palo, you will have Dashboard looks like this:
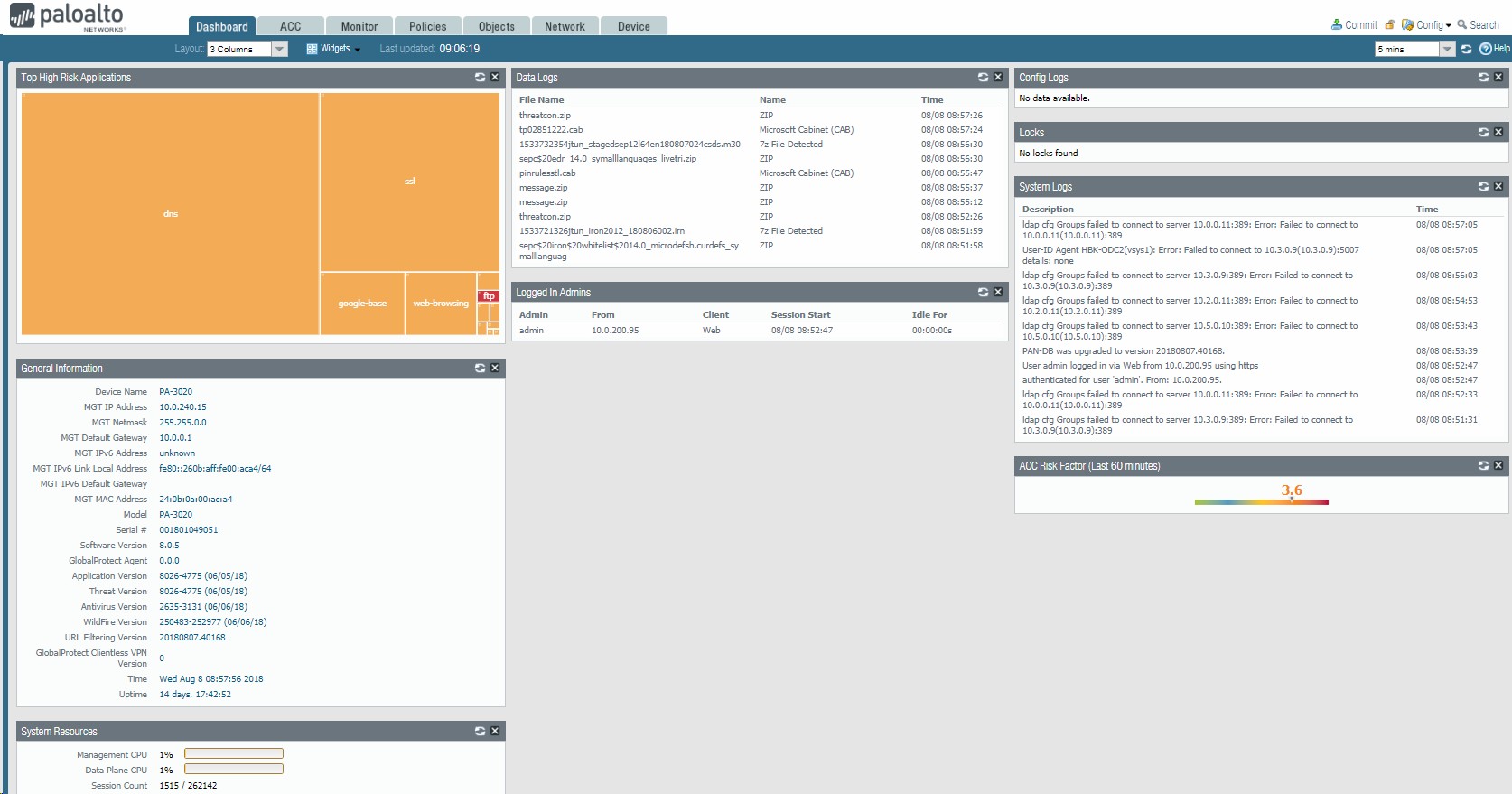
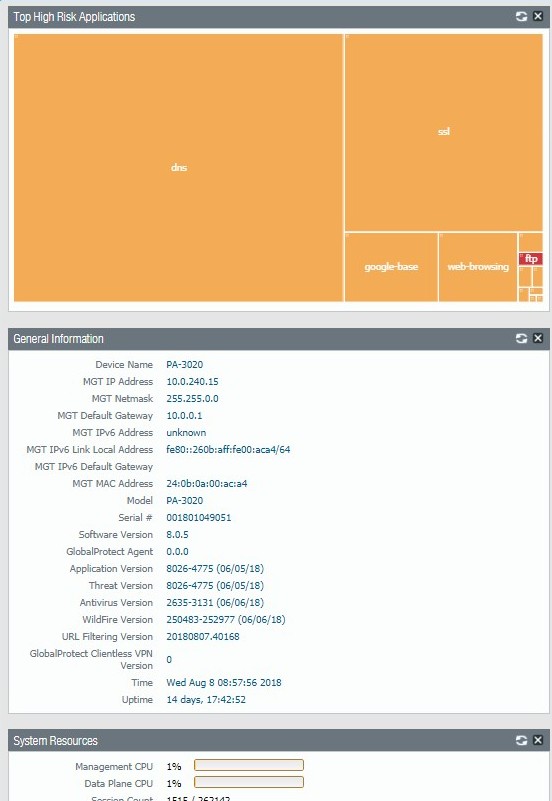
1. You can view Top High Risk Applications and General information such as device IP address, default gateway, Serial #, Software version, time and system resources.
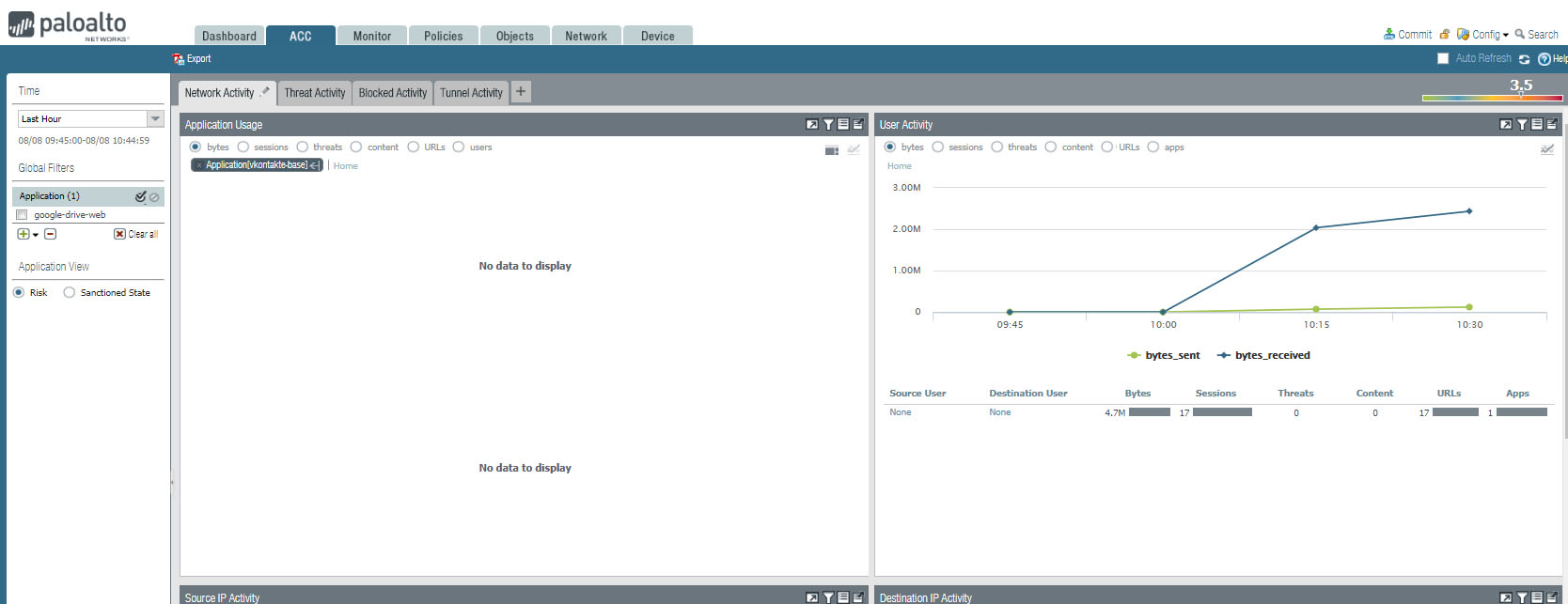
If you click High Risk Applications, it will popup Network Activity. You can High Risk App Usage, user Activity.
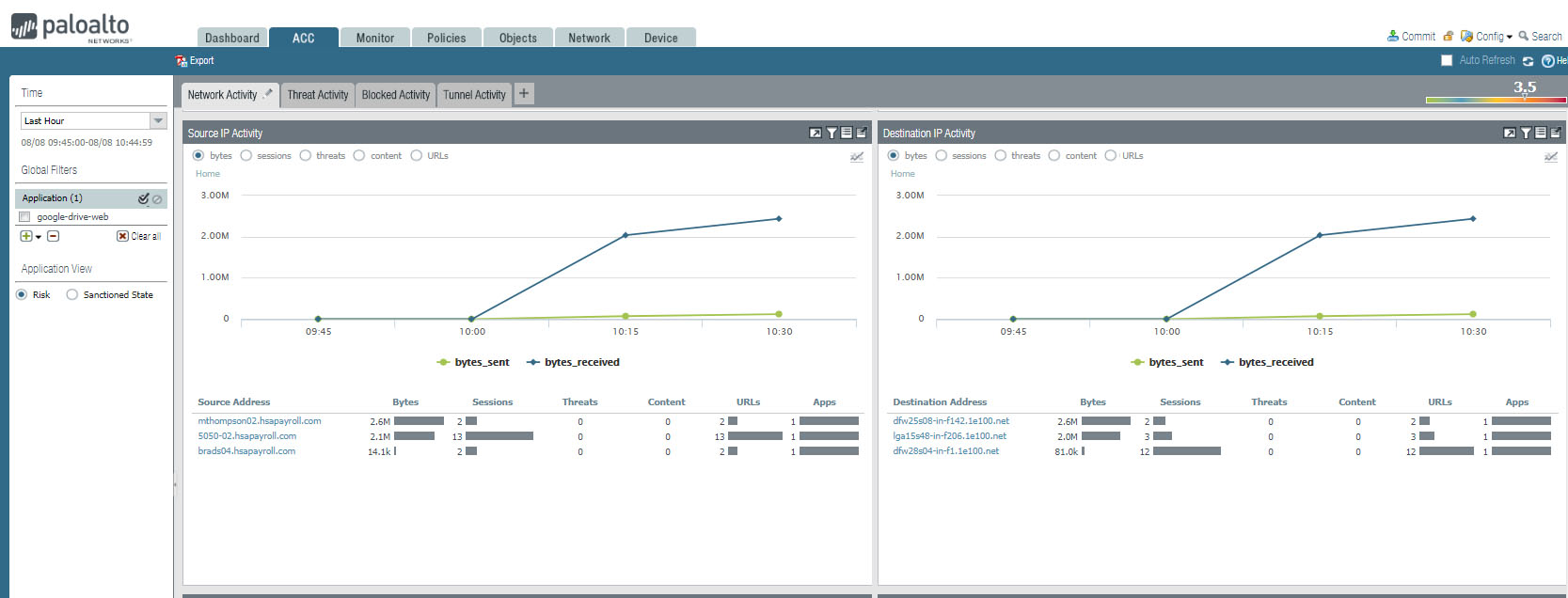
You can also view Source IP Activity, Destination IP Activity, Source regions, Destination Regions.
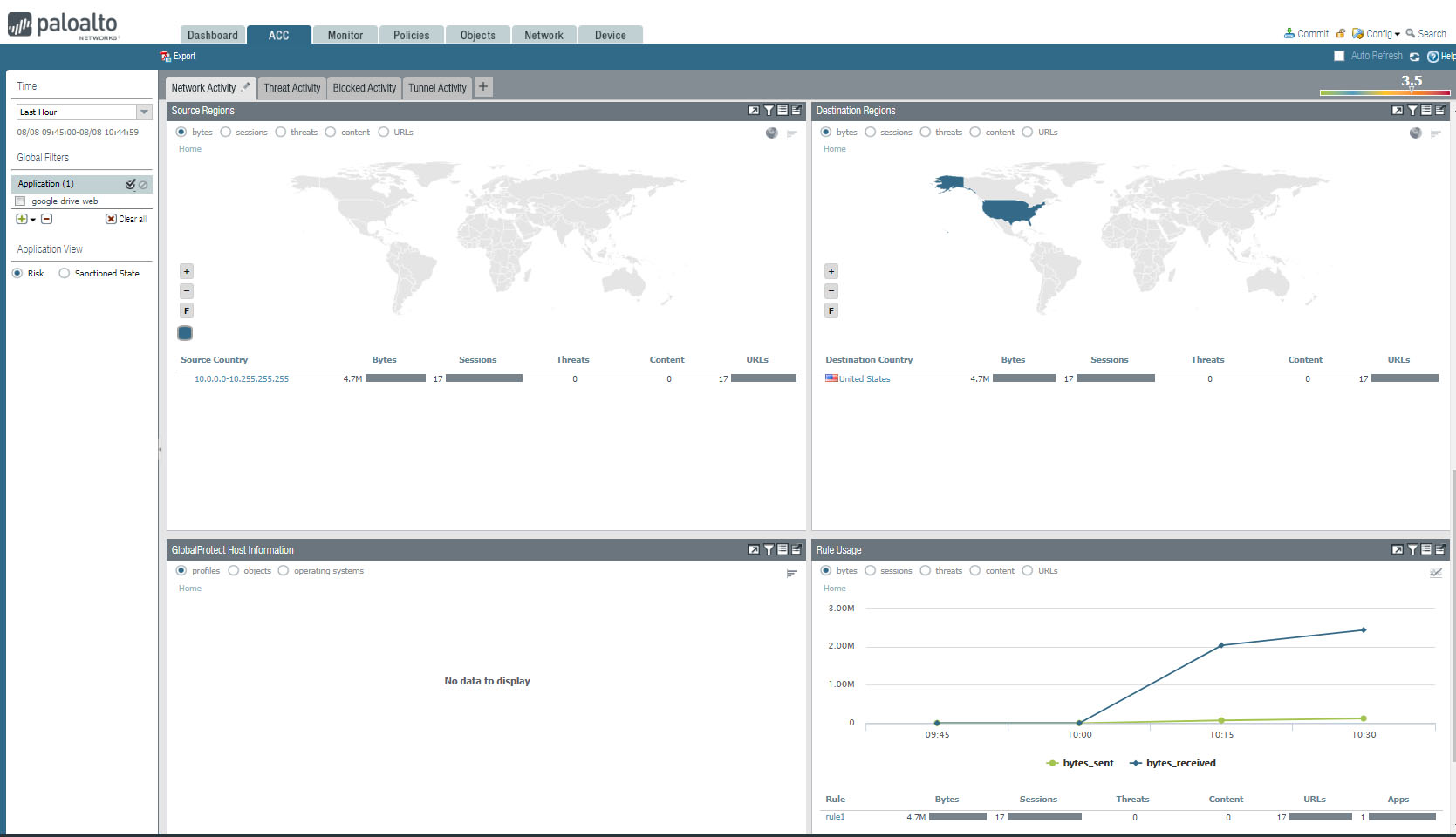
2. You will have Data logs and Logged In Admins information.
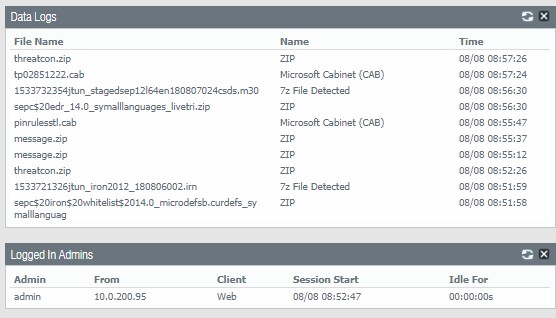
3. You will also have config Logs, Locks. System Logs information.
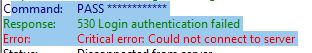
Problem to establish FTP connection
2. If you see 530 Login authentication failed lik ethis one:
Command: PASS ************
Response: 530 Login authentication failed
Error: Critical error: Could not connect to server
Make sure you have entered correct host name and password.
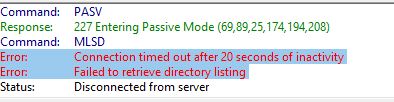
2. If you receive timeout message:
Error: Connection timed out after 20 seconds of inactivity
Error: Failed to retrieve directory listing
Make sure you enter the correct host name, port number, Encryption settings, username and password.
3. Also make sure your firewall doesn’t block the FTP traffic.
Please refer to this link for how to configure FTP client: How to configure FTP client
How to configure Filezalla FTP client
In this example, we will show you how to configure Filezilla FTP client connecting to your FTP server on bluehost.
1. Download and install Filezilla.
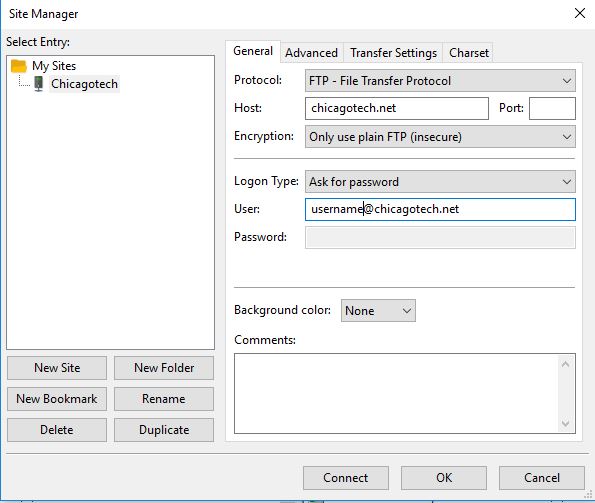
2. After running Filezilla, open Site Manager from file.
3. Enter you FTP server, for example Chicagotech.net, port 21, Only use plain FTP (insecure) in Encryption line (note: plain FTP is bluehost uses now), Ask for password in Logon Type, username@yourdomainname.
4. Click Connect. That will popup for the password.
5. If everything setup correctly, you will see “Directory listing of “/public_html” successful and “Connected established”.
How to make domain from federated to standard
Situation: A small company decide to remove their ADFS service from the domain because they use Office 365 only and Office 365 provides password hashes that handles the user authentication.
Resolution: To disable ADFS service or make the domain from Federated to standard, please run these powershell commands:
Connect-MsolService
Get-MsolDomain
Convert-MsolDomainToStandard -DomainName
Here DomainName is your company domain. For Chicagotech.net the command will be
Convert-MsolDomainToStandard -Chicagotech.net
ADFS server issue
Our ADFS server (In LAN) and ADFS Proxy server (in Azure) have a problem. The Outlook and phone keep popup for credentials. We open a case wit Office 365 team. This is what they email to me: “we found the public IP address belongs to azure machine and requests were getting dropped while forwarding to on premise environment. As we are not trained on Azure networking part so we suggested you to open a ticket with azure team. Please update us in case of our assistance/collaboration required while working with azure team”.
Relius Web Site down
Situation: the client has a Website down issue.
Troubleshooting:
I don’t see many related events in the Event Viewer. However, I do see 6 Windows updates waiting for installing. We will schedule to install them.
To fix the problem, first of all, login the Relius web server using administrator credentials. Go to Services and restart IIS Admin Service and World Web Publishing Service.
If above doesn’t fix the problem, restart the Relius web server. It is better to restart it onsite because the site may hang and need press Enter key in console.
Routing on SonicWall doesn’t work
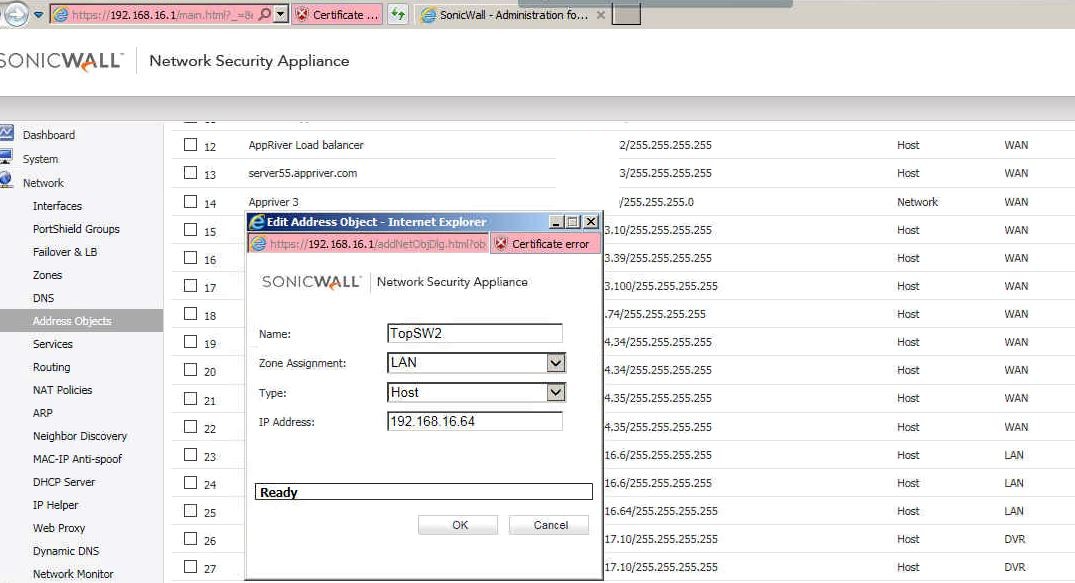
Situation: the client created VLANs in their network and configured routing on SonicWall, but the routing doesn’t work and VoIP VLAN can’t access the Internet and data VLAN can’t access the VoIP VLAN.
Troubleshooting: The gateway they tried to add for the routing policy is using VLAN VoIP Ip address (192.169.20.1) on the switch instead of data VLAN IP address (192.168.16.64).
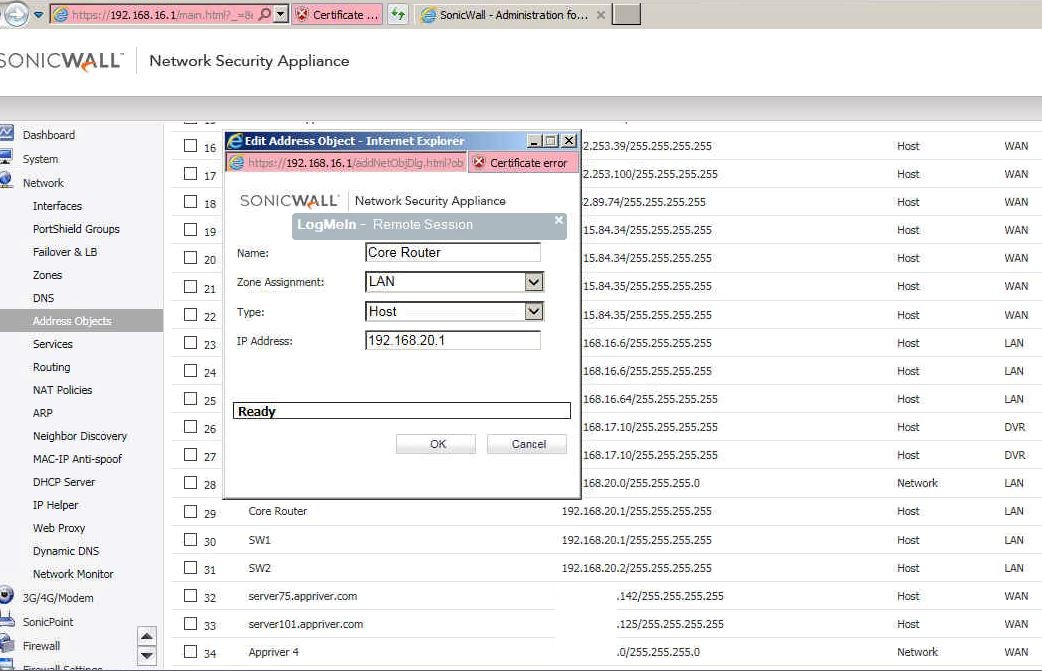
Since the default gateway is in the data VLAN (192.168.16.1), we create a new network object using switch data IP address (192.168.16.64) and replace the IP address 192.168.20.1. That fixes the problem
More details can be found this link: How to configure routing on SonicWall