Situation: The client has Paloalto Firewall running GloablProtect VPN and Site-to-site VPN to AWS tunnel. The user on office can’t access the AWS tunnel but VPN user.
Troubleshooting: 1. Monitor shows aged-out.
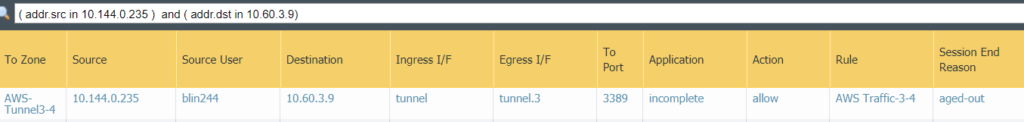
2. The detail view shows, bytes received is 0.
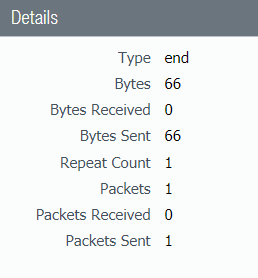
Conclusion: AWS blocks VPN IP addresses. Have AWS configure their route for VPN IP addresses.