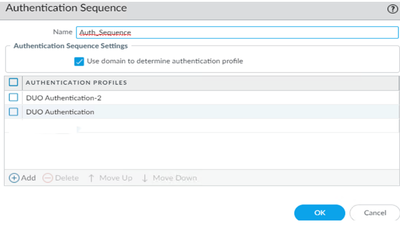
I configured DUO Proxy for GloablProtect MFA redundancy on our PA 850 firewall using Authentication Sequence. This post shows how I configured: Configure two duo proxy servers for Palo alto firewall MFA redundancy – Net/PC How to (howtonetworki…
The problem I have is when the top Authentication profile or DUO Proxy server is down, then the user can’t login to GloablProtect. The DUO Proxy server and PA authentication profile is not the issue because I can run the test command successfully.
test authentication authentication-profile <authentication-profile-name> username <username> password
Alos, if I move the second profile (DUO Authentication-2 in my example) to the top, it works.
The problem is if the top authentication DUO proxy server (DUO Authentication-2) is down, no one can’t login. MONITOR>Logs>System doesn’t have authentication information. If I move the second authentication profile (DUO Authentication in my example) to the top, then it works again. I think it is Authentication Sequence problem but can’t figure out how to fix it.
Troubleshooting:
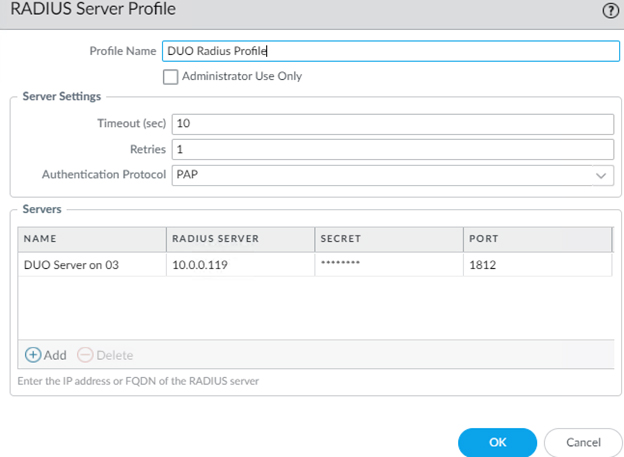
By default, GlobalProtect’s timeout is 30 seconds. If you setup timeout 30 (seconds) x 3 (retries), Authentication Sequence may not work or timeout.
You’ll need to adjust things a bit to account for the delay being introduced by the authentication sequence and the down host. This setting works for us.
On the first RADIUS Profile
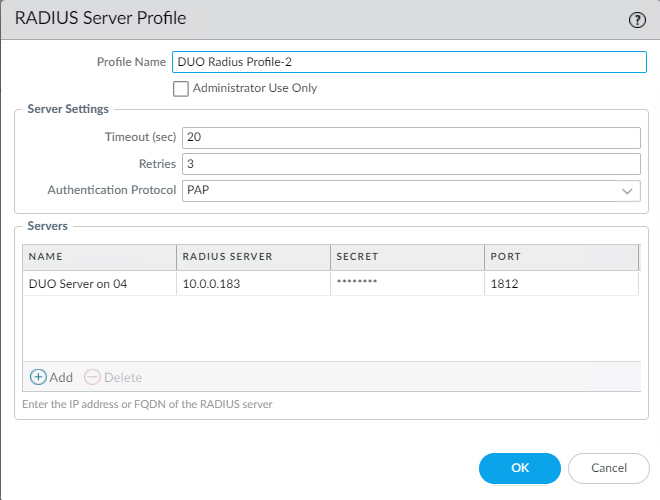
On the second RADIUS Profile.
Please refer to this document: