Situation: The client just configures MFA for their AD users to login GloablProtect. However, AD users can’t login.
Troubleshooting: In Monitor>System, it shows Failed authentication for user: Reason User is not in allowlist..
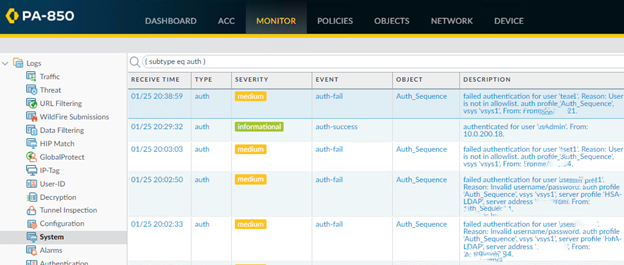
Resolution: Quoted from Palo Alto networks article:
If the allow list is changed to have “all” rather than specific groups, the user authenticates fine.
Resolution
This happens where the device might have been previously configured as a multi-vsys device. If, at that time, the authentication profile was created as a “shared” authentication profile, this would work fine. When the device configuration changes to be a single vsys device, the authentication profile may still be a “shared” profile (but with the single vsys). The device is no longer able to read the “shared” authentication profile.
When troubleshooting, run the following CLI command to show that the users are part of the group:
> show user group name <name>
When this group is referenced in the menu for the authentication profile, the user fails authentication. To get around this issue, create an authentication profile that is not shared and is vsys specific. The authentication profile then reads the groups correctly and authentication will work correctly, as the users are read as part of the group.
Some common server issues include:
- The wrong IP address is entered in the RADIUS server configuration.
- The shared secret is mis-typed. Do not paste the password into the Secret field.
- The wrong IP address is entered in the RADIUS server client configuration.
- The Radius server policy may be invalid due to:
- Wrong Windows group
- NAS-IP address
- PAP
Events can be viewed on the RADIUS server in the event viewer > system logs > IAS