Situation: The company is migrating their Cisco ASA site to site VPN connecting to Azure to PA-850. The consultant copy and configured PA-850 IPSec configuration. However, can’t establish the connection. The log shows no return.
Troubleshooting: We called Microsoft Azure support and compare Azure configuration against PA. There are twio problems.
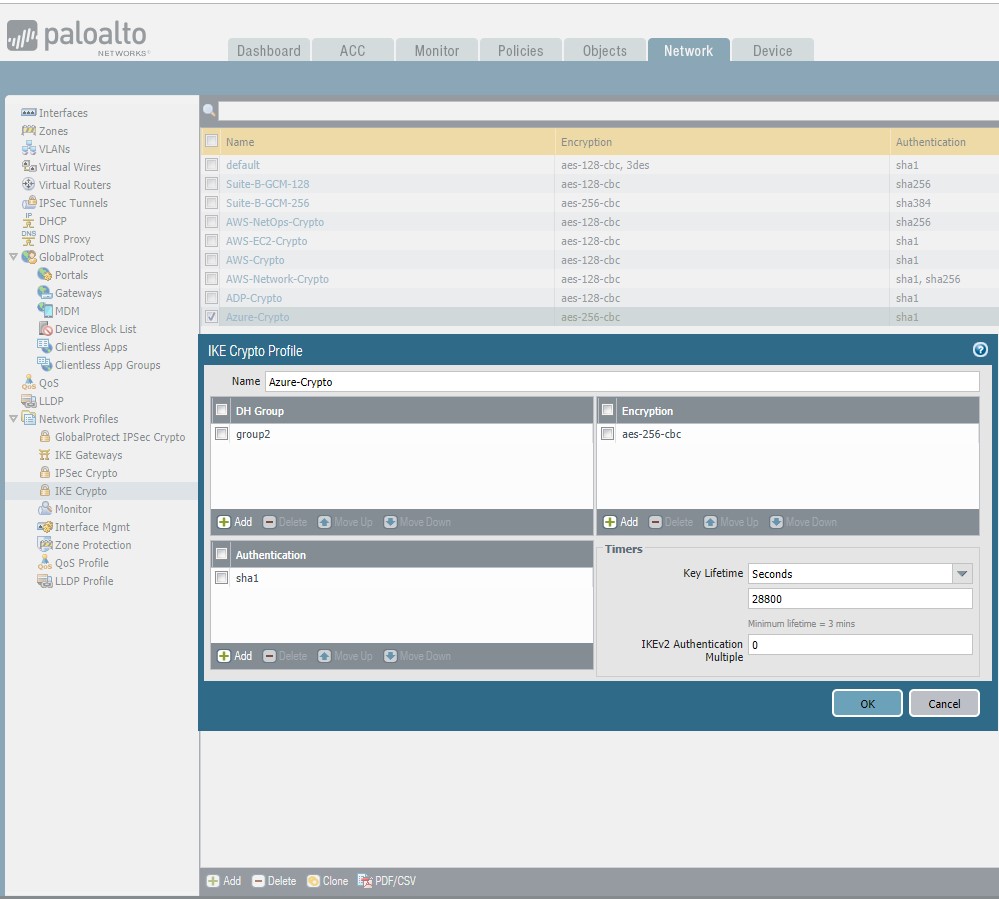
- By default, PA IKE Crypto Profile are set like these:
DH Group: group2 Encryption: aes-256-cbc, 3des Authentication: sha1, sha256.
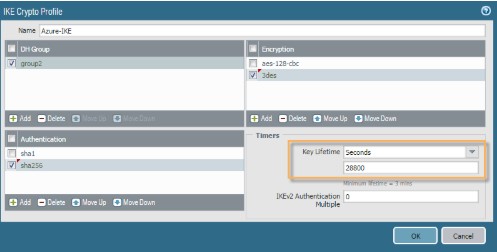
However, the PA document also says: A new crypto profile can be defined to match the IKE crypto settings of Azure VPN. This is Azre VPN settings:
2. When configuring IPSec Crypto Profile, the Lifeszie is 102,400,000. However, we can’t enter this number on PA. The value for PA is 1-65535. To fix this problem, both Azure and PA VPN need to configure Dynamic Routing instead of Static Routing.
In conclusions: 1. Must read the configuration guide carefully. 2. Copy the configuration from Cisco ASA configuration may not work. 3. PA configuration article could be obsolete.